Subscribe to Receive Updates
Join hundreds of business leaders and get our perspective on critical issues delivered to your inbox..

As more businesses migrate their operations to the cloud, the importance of robust cloud security cannot be overstated. The cloud offers unparalleled benefits in terms of scalability, cost-efficiency, and accessibility, but it also introduces significant security risks that can compromise sensitive data if not effectively managed. Understanding and implementing effective cloud security solutions is crucial for protecting a company’s data against cyber threats and ensuring compliance with regulatory requirements.
Cloud security refers to the policies, controls, procedures, and technologies that work together to protect cloud-based systems, data, and infrastructure. From securing data in transit to defending cloud applications against unauthorized access, cloud security encompasses a broad spectrum of practices designed to maintain data privacy, safeguard data integrity, and ensure access reliability.
At its core, cloud security is concerned with three fundamental aspects:
Cloud environments face a unique set of security threats and challenges:
By addressing these risks with comprehensive security measures, companies can protect data in the cloud and maintain the trust of their clients and partners. In the following sections, we will explore specific cloud security solutions and best practices to achieve this goal, emphasizing the role of managed IT service providers in enhancing cloud security capabilities.
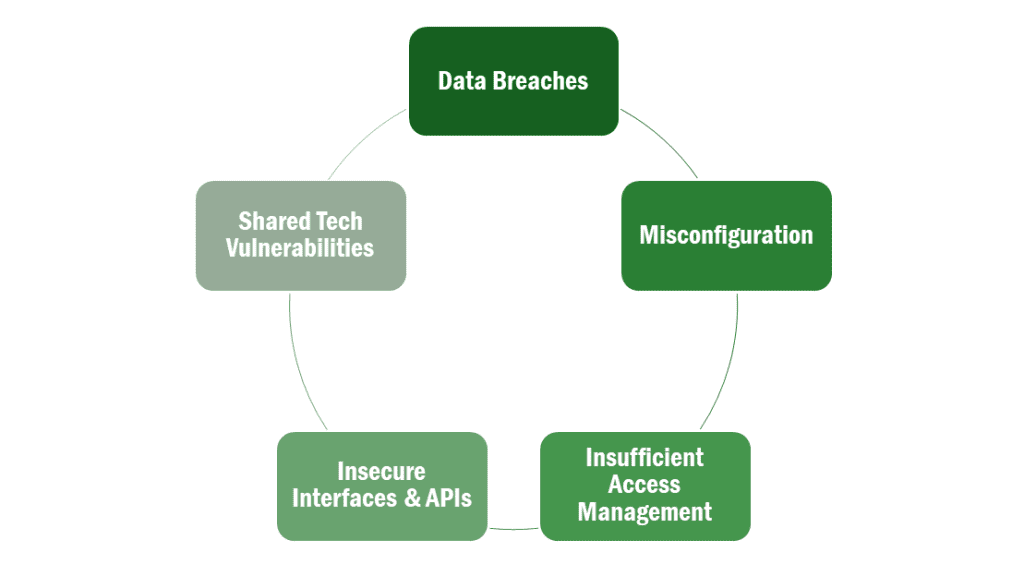
As organizations transition to cloud computing, they must employ robust cloud security solutions to safeguard their data and systems. These solutions vary widely, encompassing software, hardware, and strategic practices designed to protect cloud infrastructure and data from various threats. Here we discuss several critical solutions that form the backbone of effective cloud security.
Effective cloud security involves not only selecting the right tools but also implementing them strategically:
Despite the availability of advanced security solutions, organizations often face challenges in implementation, such as:
Managed IT service providers play a crucial role in overcoming these challenges. They offer the expertise and resources necessary to implement comprehensive security solutions efficiently. In the next section, we will delve deeper into how these providers can enhance cloud security, particularly focusing on real-time monitoring, incident response, and compliance management.
From cloud selection and migration to deployment and management, our comprehensive cloud services are designed to help your business scale effectively.
In today’s complex cybersecurity landscape, managed IT service providers (MSPs) are invaluable allies for businesses seeking to strengthen their cloud security. MSPs specialize in handling and securing IT infrastructures, offering a range of services that can significantly improve an organization’s ability to prevent, detect, and respond to security threats. Here’s how MSPs can bolster your cloud security.
Choosing the right MSP is critical. Consider these factors when selecting an MSP to enhance your cloud security:

Partnering with an MSP offers numerous benefits:
Leveraging the services of a Managed IT service provider can significantly enhance your organization’s cloud security, providing not just protection but also strategic advice tailored to your specific needs.
Navigating the complex regulatory landscape is a critical aspect of cloud security. Compliance is not merely a legal obligation but also a cornerstone of trust and reliability in business operations. Here, we will explore the key regulations affecting cloud security and how organizations can ensure compliance through effective security measures.
Many industries, especially those handling sensitive information like healthcare and finance, are subject to strict regulatory requirements concerning data security and privacy. Key regulations include:
To meet these and other regulatory requirements, organizations must implement a range of cloud security measures:
Achieving compliance in the cloud can be challenging due to:

Managed IT service providers can be instrumental in helping organizations navigate these challenges. They offer expertise in regulatory compliance specific to various industries and can assist in implementing the necessary security measures. Additionally, they can manage relationships with cloud vendors to ensure compliance across all services.
Maintaining compliance in cloud security is an ongoing process. This involves understanding regulatory requirements, implementing appropriate security measures, and continually monitoring and adapting to new regulations. With the help of knowledgeable partners like Managed IT service providers, organizations can not only meet these requirements but also strengthen their security posture and protect their valuable data.
Cloud security is an essential component of modern business operations, protecting sensitive data and ensuring compliance with stringent regulatory standards. Employing robust cloud security measures is not merely about defense but also about enabling your business to thrive and innovate securely in a digital-first world.
At thirtyone3 technology, we understand the complexities and challenges of securing cloud environments in healthcare. Our expertise in IT consulting and management services allows us to provide tailored solutions that not only meet regulatory requirements but also align with your strategic business objectives.
Our goal is to empower your organization to harness the full potential of cloud technologies safely and effectively. For more information on how we can assist with your cloud security needs or to schedule a consultation, please fill out our contact form or contact us at 623.850.5392.
Let us help you secure your cloud environment and ensure your data’s integrity and confidentiality. By adopting these comprehensive cloud security strategies and partnering with seasoned professionals, you can confidently navigate the complexities of the cloud, ensuring that your company’s data is protected against the evolving landscape of cyber threats.
Join hundreds of business leaders and get our perspective on critical issues delivered to your inbox..