Financial advisory firms in Phoenix manage highly sensitive client data including investment portfolios, retirement plans, and tax records.
That makes them prime targets for cyberattacks even if many advisors assume their firm is too small or well-protected to be at risk. The reality is that confidence in basic IT protections often leads to gaps that hackers exploit.
This insight examines five common cybersecurity assumptions that financial advisors make every day. You will learn what real protection requires and how thirtyone3 helps firms like yours stay compliant, secure, and audit ready.
- 1. Assumption 1: “Our IT Provider Handles Everything”
- 2. Assumption 2: “We’re Too Small to Be Targeted”
- 3. Assumption 3: “Compliance Equals Security”
- 4. Assumption 4: “We Already Use MFA and Backups”
- 5. Assumption 5: “Our Team Knows Better Than to Click Suspicious Links”
- 6. What Financial Advisors Actually Need
- 7. Conclusion
- 8. Need Help Getting Started?
- 9. Further Reading
- 10. Related Articles
Assumption 1: “Our IT Provider Handles Everything”
For many financial advisory firms, the relationship with their IT provider feels like a safety net.
You file tickets, they respond.
Emails get delivered. Computers get updated.
Everything seems to work.
So it is easy to assume that cybersecurity is part of the deal.
But here is the truth. Most IT providers focus on functionality, not security. Their job is to keep your systems running, not to build walls, monitor threats, or respond to breaches.
That is like assuming your building’s janitor is also your security guard, capable, reliable, but hired for a different purpose.
What General IT Support Misses
Generalist IT firms often skip critical cybersecurity layers including
- Proactive vulnerability scans
- Endpoint detection and response tools
- Security Information and Event Management (SIEM)
- Role-based access controls
- Compliance tools like PCI reporting and audit logs
When these gaps exist, hackers find them because they are looking for firms exactly like yours.
Cybersecurity for financial advisors is about protecting trust. Your clients share everything with you, and they expect that data to stay locked down. That requires more than patching software and rebooting servers. It requires a security-first mindset.
Explore our Managed Security Services to see what is actually covered and how thirtyone3 helps firms close the gap between general IT support and real protection.

Assumption 2: “We’re Too Small to Be Targeted”
Many small financial advisory firms believe cybercriminals only go after the big guys like major banks, insurance giants, or enterprise wealth managers. But in today’s threat landscape, size is not protection.
In fact, small firms are often targeted more frequently because attackers assume they lack sophisticated defenses.
Hackers know that smaller firms often outsource general IT and operate with limited internal oversight. That makes them easy targets for phishing, ransomware, and social engineering schemes.
According to guidance from FINRA on cybersecurity threats, small firms are increasingly targeted because they manage sensitive financial data yet often lack layered protections or formal risk management strategies.
The Local Reality in Phoenix
Phoenix has hundreds of 10-to-150-person financial firms, many with no in-house IT staff. If your firm fits that profile you are likely already on the radar of automated tools scanning for weaknesses.
At thirtyone3 we help firms eliminate those vulnerabilities through continuous monitoring, threat detection, and compliance-grade protections. Your size should never be your weakness.
Assumption 3: “Compliance Equals Security”
Passing a compliance audit often feels like proof that a firm’s cybersecurity is solid. But compliance and security are not the same. One proves you met requirements at a point in time. The other ensures you are protected all the time.
An audit might confirm that your backups exist but not whether they are encrypted, regularly tested, or immune to ransomware. It might check for access controls but not whether they are actively monitored.
Why the Gap Matters
Compliance frameworks change slowly. Threats evolve quickly. Treating compliance as the finish line instead of the starting point puts your firm at risk.
That is why leading advisory firms turn to providers who go beyond the checklist. At thirtyone3 our proactive IT management helps financial advisors stay ahead of attackers and regulators. We protect your firm not just from penalties but from real-world breaches.

Assumption 4: “We Already Use MFA and Backups”
It is true that multi-factor authentication and backups are important. They are foundational tools. But relying on them alone creates a false sense of security.
MFA protects access and backups provide fallback. But neither stops attackers from using vulnerabilities to access your network or steal client data.
Security Needs Layers
A modern cybersecurity approach includes
- Endpoint detection and response
- Vulnerability scanning
- SIEM tools to monitor and alert in real time
- Role-based access and privilege controls
- Regular training and policy reviews
As noted in this SIEM overview for financial firms, security tools like SIEM offer real-time visibility into threats helping prevent breaches before they cause damage.
At thirtyone3 we build these layers into every financial services deployment. You get more than backup. You get defense.
Assumption 5: “Our Team Knows Better Than to Click Suspicious Links”
Trusting your team is important. But even experienced professionals fall for phishing tactics. And modern phishing is more believable than ever with emails mimicking clients, vendors, or internal staff.
Good Judgment Is Not a Strategy
Security awareness is not a one-time meeting. It must be reinforced regularly. That includes
- Quarterly phishing simulations
- Interactive cybersecurity training
- Role-based threat briefings
- Easy reporting protocols
At thirtyone3 we help firms like yours build a culture of cyber vigilance. Your team becomes part of the solution, not your biggest vulnerability.
What Financial Advisors Actually Need
Partial protection is no longer enough. Today’s threats demand more than a helpdesk or compliance checkbox.
Here is what a modern cybersecurity strategy looks like:
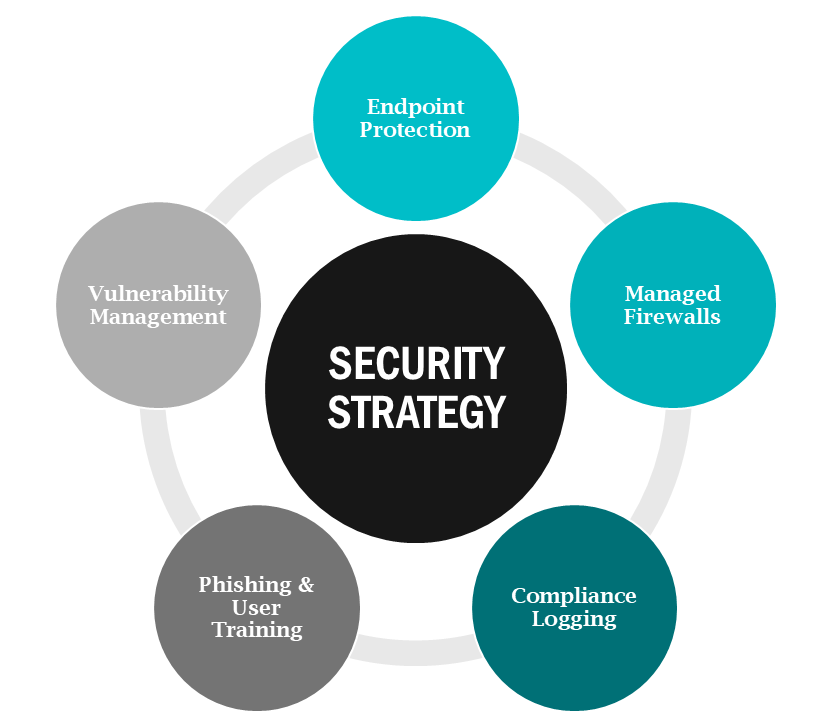
At thirtyone3 we deliver this entire stack in a way that fits your size, budget, and compliance needs especially for firms in the Phoenix Metro market.
Conclusion
Every firm thinks they are secure until something goes wrong. The assumptions covered in this Insight are common but they are also costly.
You do not need to wait for a breach to start protecting your business. Let thirtyone3 help you assess where you stand and build a smarter cybersecurity strategy.
Get started with a free cybersecurity consultation today.
Need Help Getting Started?
Further Reading
- thirtyone3 technology: The Hidden Costs of Cheap IT Support
Breaks down how low-cost IT solutions often lead to higher long-term expenses due to downtime, poor service, and unresolved risks. - thirtyone3 technology: The Hidden Costs of Cheap IT Support
Breaks down how low-cost IT solutions often lead to higher long-term expenses due to downtime, poor service, and unresolved risks. - thirtyone3 technology: The Hidden Costs of Cheap IT Support
Breaks down how low-cost IT solutions often lead to higher long-term expenses due to downtime, poor service, and unresolved risks. - thirtyone3 technology: The Hidden Costs of Cheap IT Support
Breaks down how low-cost IT solutions often lead to higher long-term expenses due to downtime, poor service, and unresolved risks.

