IT security risk management is the structured process of identifying, assessing, and controlling threats to an organization’s digital environment.
These risks can come from many sources, including cybercriminals, system vulnerabilities, employee mistakes, and even trusted vendors. They can impact every part of the business.
Modern organizations rely on interconnected systems, cloud platforms, remote access tools, and third-party applications to operate efficiently. While these technologies create opportunities for growth and collaboration, they also increase exposure if they are not monitored and secured.
Cyber threats are no longer limited to large enterprises. Small to mid-sized businesses are now among the most frequently targeted. Attackers often assume these organizations have fewer internal IT resources, limited monitoring capabilities, and inconsistent security controls.
A single successful breach can interrupt operations, reduce revenue, damage customer trust, and create financial strain that is difficult to recover from.
This is why IT security risk management must be treated as an essential business function rather than a one-time checklist. It shifts organizations from reacting to incidents to preventing them through ongoing assessment, monitoring, and mitigation.
The Cybersecurity and Infrastructure Security Agency (CISA) provides guidance to help organizations understand and establish structured security risk practices in its Risk Management Overview resource, which outlines how to build a strong and resilient security posture.
At thirtyone3 technology, we help organizations move from uncertainty to confidence by taking a proactive approach to cybersecurity.
Through continuous monitoring, systems hardening, strategic assessments, and managed security services, we support businesses in protecting their data, their operations, and their reputation.
- 1. Why Is IT Security Risk Management Crucial for Modern Organizations?
- 2. What Are the Key Steps in an Effective IT Security Risk Management Program?
- 3. What Are the Most Common IT Security Risks Facing Businesses Today?
- 4. How to Build an Effective IT Security Risk Management Program
- 5. What Role Does Managed IT Play in IT Security Risk Management?
- 6. How Does IT Security Risk Management Protect Business Continuity?
- 7. What Tools and Frameworks Strengthen IT Security Risk Management?
- 8. How Should Businesses Manage Vendor and Supply Chain Risk?
- 9. How Can Businesses Build a Culture of Security Awareness?
- 10. Why Is IT Security Risk Management Worth the Investment?
- 11. Need Help Getting Started?
- 12. Further Reading
- 13. Related Articles
Why Is IT Security Risk Management Crucial for Modern Organizations?
The modern business relies on technology to operate. Operations, communication, customer engagement, financial transactions, and service delivery all depend on stable and secure digital systems.
When these systems are disrupted, business is disrupted. This is why IT security risk management is not simply an IT responsibility. It is a core business function that protects revenue, reputation, and the continuity of daily operations.
Cyberattacks have become more frequent and more sophisticated. Small and mid-sized organizations are often targeted because they may not have dedicated internal security teams or formalized cybersecurity programs.
Threats such as phishing, ransomware, and credential theft can move quickly and quietly, often going unnoticed until damage has already occurred. The cost is not only financial. Downtime, loss of trust, and the interruption of critical services can have long-lasting impacts.
An effective IT security risk management program ensures the organization understands where its vulnerabilities exist and what controls are needed to reduce exposure.
It also ensures that safeguards are reviewed and updated regularly as risks evolve. This continual improvement approach supports better decision making, strengthens resilience, and ensures the business is prepared rather than reactive.
For many organizations, partnering with a managed service provider such as thirtyone3 technology ensures that security is monitored and managed daily.
This reduces the burden on internal staff and strengthens the organization’s ability to respond quickly and confidently when threats arise.
What Are the Key Steps in an Effective IT Security Risk Management Program?
An effective IT security risk management program follows a structured approach that helps organizations understand where risks are present, how serious those risks may be, and what controls are necessary to reduce potential impact. While each organization is unique, the core steps are consistent.
The first step is to identify the systems and assets that support daily operations. This includes workstations, servers, cloud applications, network devices, and business data.
Understanding what needs to be protected provides a clear foundation for building a focused security strategy. Organizations often begin this analysis during a Security Risk Assessment, which is part of thirtyone3 technology’s Managed IT Services program.
The second step is to assess vulnerabilities and potential threats. This may include evaluating system configurations, reviewing user access practices, checking for outdated software, and analyzing where sensitive information is stored.
Guidance from the NIST Guide for Conducting Risk Assessments (SP 800-30) can help organizations create consistency in how risks are evaluated and prioritized.
The third step is to implement security controls that reduce or eliminate potential exposure. These controls may include antivirus and endpoint protection, multifactor authentication, secure network configuration, regular data backups, and ongoing employee security awareness training.
thirtyone3 technology supports these measures through our Cybersecurity and Threat Protection services, which include continuous monitoring and response.
The final step is ongoing review and improvement. Since cyber threats continue to evolve, security practices must evolve alongside them. Organizations benefit from scheduled evaluations, updates to security tools, and periodic training to keep staff informed.
Many businesses rely on thirtyone3’s Virtual CIO Services for strategic oversight and long-term planning.
Industry research and insights, such as those published through the Microsoft Security Blog – Risk Management Insights can also help organizations stay informed about emerging threats and evolving best practices.
What Are the Most Common IT Security Risks Facing Businesses Today?
Every organization today faces increasing cybersecurity threats. These risks can disrupt operations, expose sensitive data, damage reputation, and lead to costly regulatory issues. Understanding the most common risks is the first step to strengthening protection.

1: Phishing and Social Engineering
Phishing is one of the most common causes of data breaches. Attackers send emails or messages pretending to be trusted sources to trick individuals into clicking malicious links or revealing login credentials. This method targets people, not systems.
2: Compromised Passwords and Credential Theft
Weak, shared, or reused passwords make it easy for hackers to break in. Risk increases when multi-factor authentication is not enabled or when passwords are stored insecurely.
3: Ransomware
Ransomware encrypts systems and blocks access until payment is made. This can lead to significant financial loss and operational shutdowns. Healthcare and small businesses are common targets due to the high value of patient and operational data.
4: Unsecured Remote Work
Remote access increases vulnerability when devices, home Wi-Fi networks, and shared computers lack proper controls and security safeguards.
5: Outdated or Unpatched Software
Failing to install updates allows attackers to exploit known vulnerabilities. Security patches are critical for preventing system breaches.
6: Insider Threats
Insider risks may be intentional or accidental. Mistakes such as sending the wrong document or failing to follow data handling procedures can expose sensitive information.
7: Cloud Misconfiguration
Cloud platforms like Google Workspace and Microsoft 365 require proper configuration. Incorrect sharing permissions or missing security controls are common sources of data leakage.
8: Weak Vendor and Third-Party Controls
When vendors or partners access your systems or data, their security practices become your risk. Without clear controls, your organization can be exposed through someone else’s vulnerabilities.
How to Build an Effective IT Security Risk Management Program
Building a strong IT security risk management program does not require more technology. It requires clarity, consistency, and alignment.
The goal is to create a system that identifies risks early, addresses them proactively, and supports the way your organization actually works.
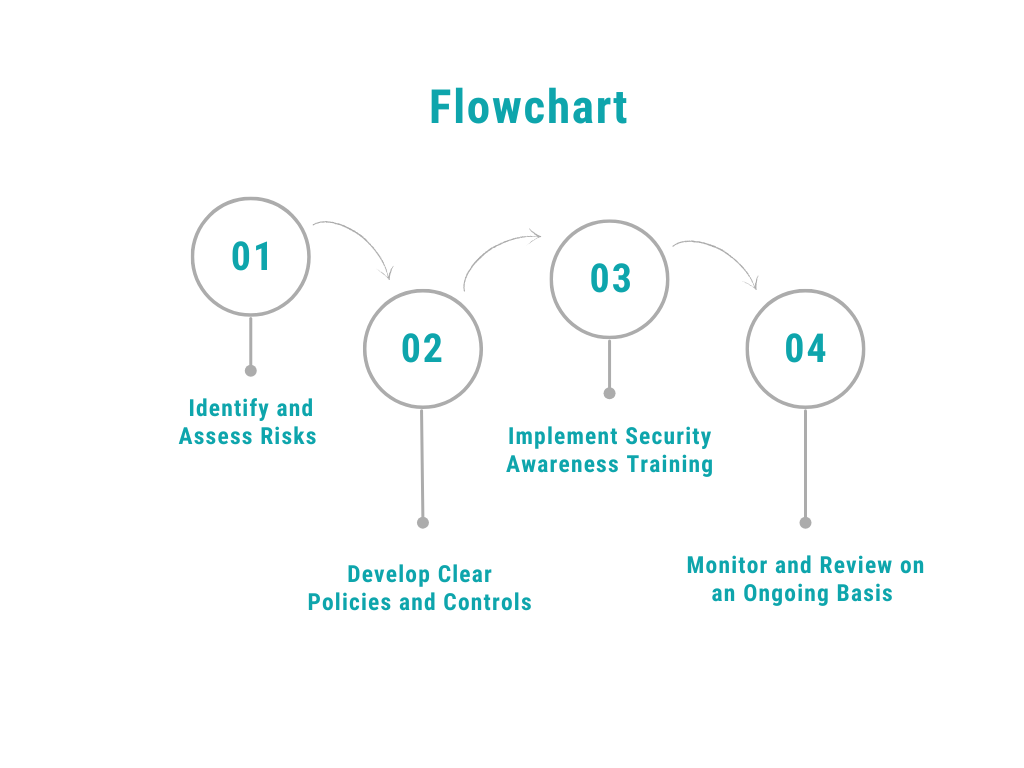
Identify and Assess Risks
Start by taking inventory of your systems, users, devices, and third-party tools. Determine where sensitive data is stored and accessed. From there, evaluate the likelihood and impact of potential threats. This process provides a clear picture of your highest-risk areas.
Develop Clear Policies and Controls
Policies ensure everyone understands expectations. Controls provide the structure to enforce them. Examples include password standards, device usage rules, and access requirements. The goal is to create consistency across the organization.
Implement Security Awareness Training
People are often the first line of defense. Regular training helps team members recognize suspicious emails, follow safe data handling practices, and understand their responsibilities in protecting organizational data.
Monitor and Review on an Ongoing Basis
Risk changes over time. New staff, new software, and evolving threats mean the environment is never static. Regular risk assessments and review meetings help keep your program current, effective, and aligned with real-world operations.
What Role Does Managed IT Play in IT Security Risk Management?
Managed IT services strengthen an organization’s security posture by providing proactive oversight and specialized expertise. Instead of waiting for issues to arise, a managed IT partner continuously monitors the network, identifies unusual activity, and addresses vulnerabilities before they become problems.
They stay current on cybersecurity threats and best practices, helping organizations adapt to changes that internal teams may not have the time or resources to track. Managed IT also supports compliance efforts by implementing and maintaining safeguards that align with HIPAA and other regulatory requirements.
This combination of ongoing protection, expert guidance, and strategic alignment helps healthcare organizations reduce risk, maintain stable operations, and safeguard the information entrusted to their care.
How Does IT Security Risk Management Protect Business Continuity?
An effective IT security risk management strategy is essential for keeping daily operations running smoothly. Business continuity depends on systems staying available, data remaining intact, and teams being able to work without disruption.
When risks are identified and addressed early, organizations are better prepared to prevent incidents that could interrupt care delivery, communication, or internal workflows.
This not only protects productivity but also maintains the confidence of patients, partners, and staff.
Reliable continuity also depends on the technologies that support resilience. Backup and disaster recovery systems ensure that data can be restored quickly if it is lost or compromised.
Endpoint protection helps safeguard the devices staff use every day, reducing the likelihood of malware or unauthorized access. Continuous monitoring adds another layer of protection by identifying unusual activity in real time, so action can be taken before it affects operations.
At thirtyone3, these capabilities are integrated through our Managed IT and Cloud Services. We support organizations by monitoring their systems, protecting their devices and networks, and maintaining secure backup environments.
This proactive approach reduces downtime, limits disruptions, and helps ensure your organization can continue operating even when unexpected challenges arise.
What Tools and Frameworks Strengthen IT Security Risk Management?
Effective IT security risk management is supported by structured frameworks that guide how organizations assess risks, implement safeguards, and respond to threats. One of the most widely recognized frameworks is the NIST Cybersecurity Framework (CSF).
It provides clear guidance across five core areas: identify, protect, detect, respond, and recover. These principles help organizations create repeatable processes for managing security risks rather than relying on reactive or patchwork solutions.
For healthcare organizations, frameworks like NIST CSF are especially valuable because they align naturally with HIPAA security expectations. They help ensure that protective measures are practical, measurable, and consistently applied across systems and teams.
At thirtyone3, we help clients apply these standards in a way that fits their real operations and their budget. This includes evaluating current security practices, identifying gaps, and building a roadmap that strengthens resilience over time.
Through our IT Consulting Services, organizations receive guidance that supports compliance, enhances security posture, and improves long-term continuity planning.
By grounding security efforts in proven frameworks, organizations can move from reacting to threats to actively managing and reducing them.

How Should Businesses Manage Vendor and Supply Chain Risk?
Vendor and supply chain risk management have become a critical part of IT security. Many organizations rely on third-party software, cloud platforms, and service providers to support daily operations.
While this creates efficiency, it also expands the number of systems and entities that may have access to sensitive information. If a vendor experiences a breach or security failure, the effects can quickly extend to your organization.
Managing this risk starts with due diligence. This includes evaluating a vendor’s security practices, understanding how they protect data, and confirming that they meet industry and regulatory requirements.
It is also important to limit the data and system access vendors receive to only what is necessary for their role. Implementing role-based access controls helps ensure external partners cannot access information they do not need.
Ongoing oversight is equally important. Organizations should periodically review vendor performance, require updates on their security posture, and adjust access if business needs change.
By maintaining structured oversight, businesses can reduce exposure and strengthen overall resilience.
How Can Businesses Build a Culture of Security Awareness?
Technology alone cannot protect an organization. People are often the first line of defense against security threats, especially in environments where daily work involves handling sensitive data.
When employees understand how to recognize suspicious activity and follow safe practices, the entire organization becomes more resilient.
Building a culture of security awareness starts with regular training that is practical, not overwhelming. This includes teaching staff how to identify phishing attempts, use strong passwords, and report unusual system behavior.
Phishing simulations can be especially effective because they allow team members to practice identifying real-world threats in a low-risk environment. Internal awareness campaigns, such as reminders during team meetings or brief monthly tips, help keep security top of mind.
The goal is not to create fear, but confidence. When employees understand how their actions contribute to protecting the organization, they become active partners in maintaining security, rather than passive participants.
Why Is IT Security Risk Management Worth the Investment?
Investing in IT security risk management strengthens an organization’s ability to operate reliably, maintain trust, and avoid costly disruptions. When systems are protected and risks are actively monitored, teams can work with confidence knowing their tools and data are secure.
This stability directly supports patient care, administrative efficiency, and organizational growth. It also reduces the financial impact of downtime, data loss, and emergency recovery efforts, which are often far more expensive than prevention.
Strong security practices also reinforce trust within the individuals and communities you serve. Patients and partners expect their information to be handled carefully and stored securely. A proactive approach helps demonstrate that protection is a priority, not an afterthought.
Healthcare organizations in Arizona also have access to valuable guidance through the Arizona Department of Homeland Security Cybersecurity Resources, which provides support for improving readiness and resilience.
These resources complement internal security planning by offering statewide standards and best practices.
Prevention is always more cost-effective than recovery. By taking steps to strengthen your security strategy now, your organization is better prepared to respond to the unexpected in the future.
If you would like support evaluating your current security posture or developing a plan that fits your operations and budget, contact us. Our team is here to help you build a stronger, more resilient security foundation.
Need Help Getting Started?
Further Reading
- NIST Cybersecurity Framework (CSF)
- Arizona Department of Homeland Security Cybersecurity Resources
- NIST Guide for Conducting Risk Assessments (SP 800-30)
- Microsoft Security Blog – Risk Management Insights
- IBM Cost of a Data Breach Report 2024
- Verizon Data Breach Investigations Report
- CISA Risk Management Overview

