Subscribe to Receive Updates
Join hundreds of business leaders and get our perspective on critical issues delivered to your inbox..

In today’s rapidly evolving digital landscape, cybersecurity has become an essential pillar of a business’ information technology (IT) strategy. As cyber threats grow more complex and sophisticated, the need for strong defense systems and proactive response strategies has transitioned from being optional to essential.
The latest statistics on cybersecurity breaches for businesses reveal several alarming trends and figures. In 2023, the United States continued to have the highest cost of a data breach at $5.09 million. The global average cost of a data breach was $4.45 million, marking a 15% increase over three years.
The impact on small to medium-sized businesses (SMBs) is also concerning. 46% of all cyber breaches impact businesses with fewer than 1,000 employees. Additionally, 61% of small to medium-sized businesses (SMBs) were targeted in 2021 alone. The most common types of attacks on small businesses were malware, phishing, and data breaches.
These statistics highlight the evolving and increasingly costly nature of cyber threats facing businesses today, emphasizing the need for robust cybersecurity measures and preparedness.
So, what happens if your business falls victim to a cybersecurity breach? Do you have a plan in place to respond effectively?
Do you know what your legal obligations are or how to recover your data?
At thirtyone3 technology, we understand the evolving cyber threat environment and have provided a streamlined guide with clear, actionable steps to mitigate risks and maintain trust in the wake of a cybersecurity incident.
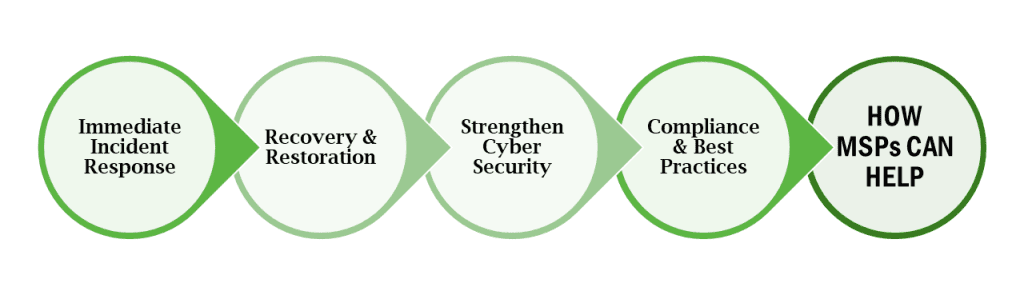
Immediate Response: Quickly isolate affected systems and assess the breach to limit damage and preserve evidence.
Coordinated Team Response: Form a multidisciplinary Incident Response Team including IT, legal, PR, HR, and executive leadership to manage the breach comprehensively.
Communication and Compliance: Maintain timely and transparent communication internally and externally while ensuring compliance with legal obligations to mitigate further issues.
Thorough Investigation and Recovery: Conduct detailed investigations to understand and rectify vulnerabilities, followed by a systematic recovery of operations.
Post-Breach Improvement: Use the incident as an opportunity to strengthen security measures, update protocols, and promote a culture of continuous security improvement.
The first moments following the discovery of a cybersecurity breach are critical. Swift and decisive actions can significantly limit the impact, helping to contain the breach and lay the groundwork for a structured recovery. Here is how your business should approach this initial phase:
The complexity of responding to a cybersecurity breach necessitates a coordinated effort from various parts of your organization. This is where the Incident Response Team (IRT) comes into play. Ideally, this team should be pre-established and include members with diverse expertise:
By swiftly containing the breach and assembling a multidisciplinary response team, your business can lay a solid foundation for a structured and effective response. The subsequent steps, which we will delve into in the following sections, will guide your organization through the intricacies of navigating the aftermath of a cybersecurity incident.
In the wake of a cybersecurity breach, clear and strategic communication, coupled with a thorough understanding of legal obligations, is paramount. This section outlines the key considerations and steps for effective communication and compliance during a cybersecurity incident.
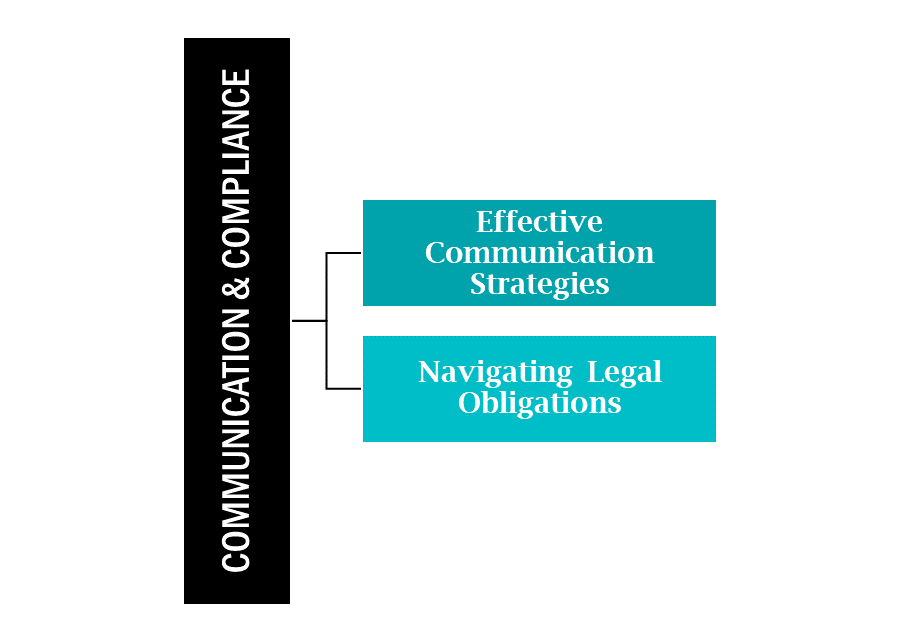
Timely and transparent communication is crucial in managing a cybersecurity breach. It helps contain the breach and maintain stakeholder trust.
Understanding and complying with legal requirements is not just about adherence to the law; it is also about protecting your organization from additional liabilities and maintaining your reputation.
By implementing effective communication strategies and adhering to legal obligations, businesses can navigate the tumultuous period following a cybersecurity breach with greater assurance and control. This approach not only aids in containing the breach and mitigating damages but also lays a foundation for recovery and rebuilding trust with stakeholders.
After establishing communication channels and ensuring compliance with legal obligations, the focus shifts to thoroughly investigating the breach and initiating the recovery process. This stage is critical for understanding the breach’s origins, scope, and for preventing future incidents.
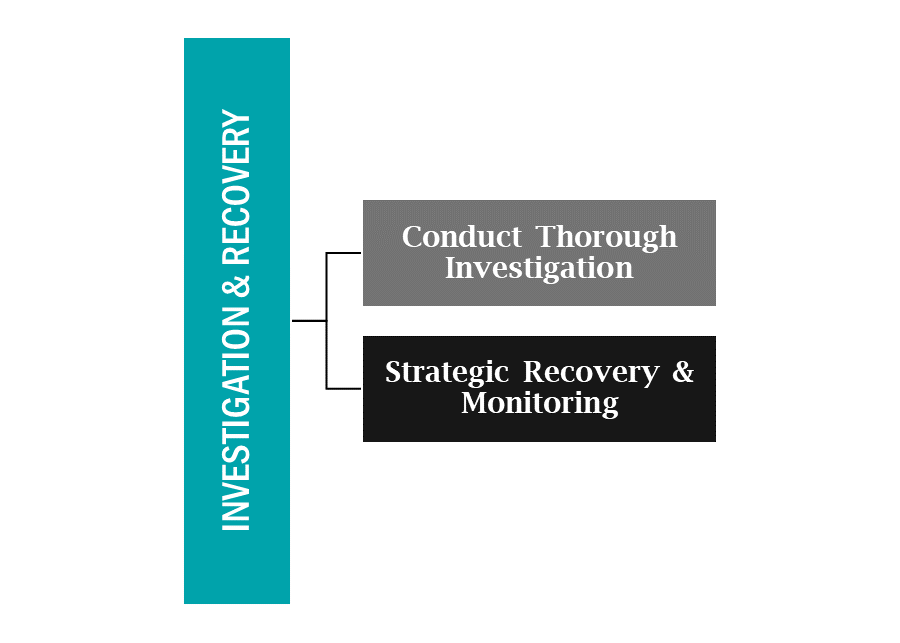
A meticulous investigation is crucial for uncovering the how, why, and what of the breach, providing insights that are vital for recovery and future prevention.
Recovery is not just about restoring systems, but also about strengthening them against future attacks. Continuous monitoring ensures that the systems remain secure and that any anomalies are detected early.
By conducting a comprehensive investigation and a structured recovery, your business can not only bounce back from the breach but also fortify your defenses against future threats. This proactive stance is key to maintaining resilience in an ever-evolving cybersecurity landscape.

The aftermath of a cybersecurity breach offers a unique opportunity for reflection, learning, and improvement. Taking proactive steps after the incident can significantly enhance your organization’s security posture and stakeholder trust.
A thorough review of the breach and the response efforts is essential for identifying strengths, weaknesses, and opportunities for improvement.
Maintaining open communication channels and demonstrating a commitment to improvement are crucial for rebuilding trust with stakeholders after a breach.
Creating a culture that prioritizes cybersecurity can significantly reduce the risk of future breaches. This involves not just technological solutions, but also people and processes.
By taking these post-breach actions and fostering a culture of continuous improvement, your business will not only recover from the incident but also emerge stronger, more resilient, and more trusted by your stakeholders.

Navigating the aftermath of a cybersecurity breach is a daunting but manageable task when approached with diligence, structure, and a forward-thinking mindset. The journey from the immediate response to post-breach improvement is not merely about recovery—it is about transforming the incident into a catalyst for strengthening organizational resilience and trust.
The path to responding and recovering from a cybersecurity breach can be complex and overwhelming. By leveraging the expertise and resources of a managed service provider (MSP) such as thirtyone3 technology, your business can adopt a structured and efficient approach to mitigate the impacts of such incidents. Here is how we can aid in this process, putting your mind at ease:
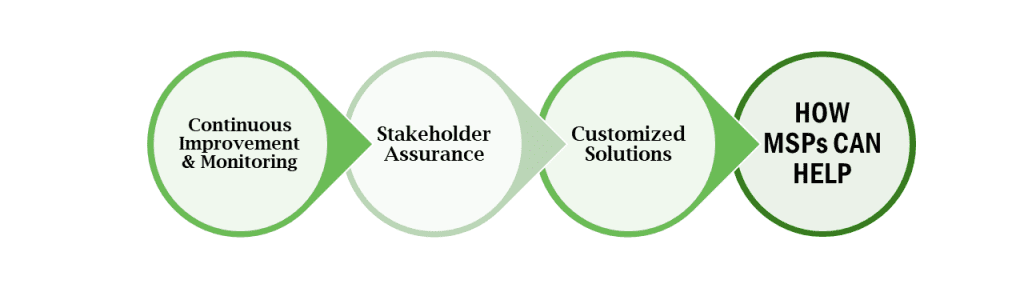
thirtyone3 technology is a leading MSP that offers comprehensive cybersecurity solutions for businesses of all sizes. Through advanced threat detection, we proactively identify and neutralize potential threats, ensuring they are intercepted before any damage occurs. With fortified firewalls, endpoint security measures, and timely application of security updates, we create a formidable barrier, preventing unauthorized access to your digital assets.
If you have questions or concerns about your company’s cybersecurity or would like to schedule a security assessment, contact our tech team at 623.850.5392 or fill out our contact form. We are here for you and happy to help!
Join hundreds of business leaders and get our perspective on critical issues delivered to your inbox..